How to Use/ Install BruteShark
HOW TO USE/INSTALL BRUTESHARK
BruteShark is regarded as Network Forensic Analysis Tool (NFAT) that performs deep processing and inspection of network traffic (mainly PCAP files). It includes: password extracting, building a network map, reconstruct TCP sessions, extract hashes of encrypted passwords and even convert them to a Hashcat format so as to perform an offline Brute Force attack.
The main goal of the project is producing solution to security researchers and network administrators with the task of network traffic analysis while they struggle to spotweaknesses that may be employed by a possible attacker to achieve access to critical points on the network.
Two BruteShark versions are available, A GUI based application (Windows) and a program line Interface tool (Windows and Linux).
The various projects within the solution can even be used independently as infrastructure for analyzing network traffic on Linux or Windows machines. For further details see the Architecture section.
What it can do
Extracting and encoding usernames and passwords (HTTP, FTP, Telnet, IMAP, SMTP...)
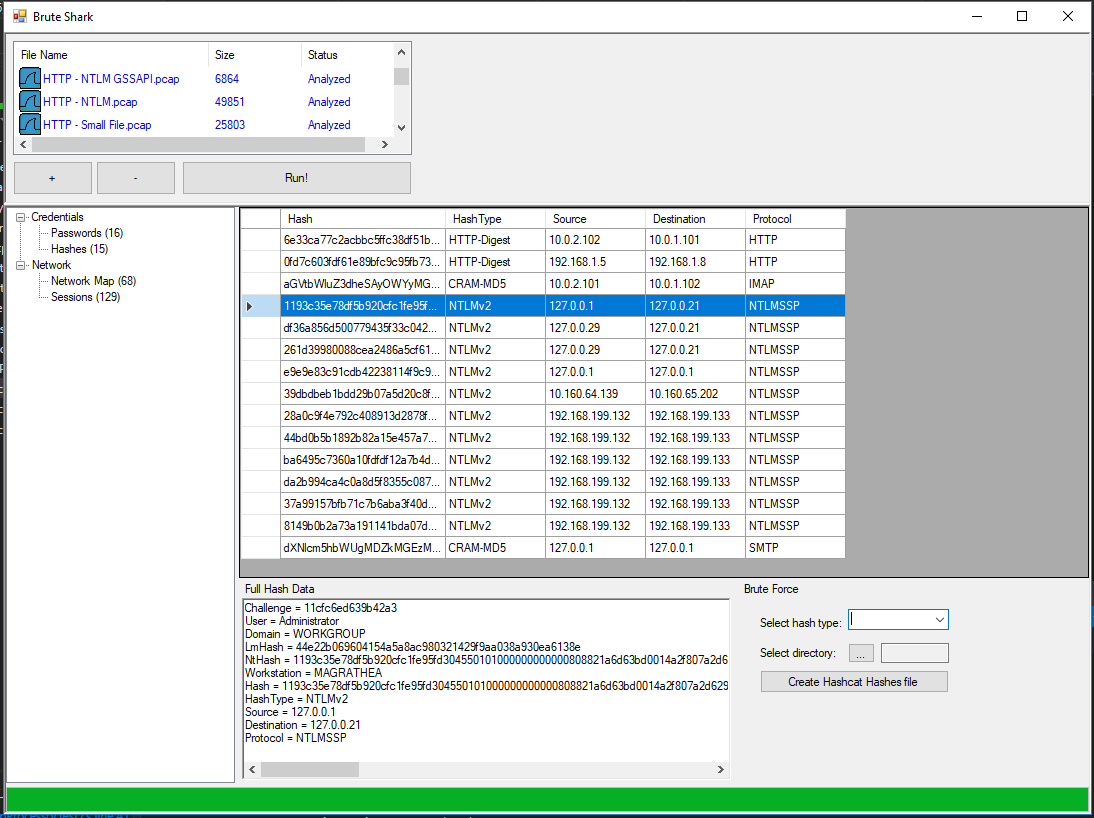
Extract authentication hashes and crack them using Hashcat (Kerberos, NTLM, CRAM-MD5, HTTP-Digest...)
Build a visible network diagram (Network nodes & users)
Reconstruct all TCP Sessions
Download
Windows - download Windows Installer (64 Bit).Linux - download BruteSharkCli.zip and run BruteSharkCli.exe using MONO:
wget https://github.com/odedshimon/BruteShark/releases/latest/download/BruteSharkCli.zip
unzip BruteSharkCli.zip
mono BruteSharkCli/BruteSharkCli.exe
Examples
BruteShark Hashes Extracting
Architecture
The solution is intended with three-layer architecture, including one or more projects at each layer - DAL, BLL, and PL. The separation between layers is made by the actual fact that every project refers only to its own objects.PcapAnalyzer (BLL)
The Business Logic Layer, answerable for analyzing network information (packet, TCP Session etc.), implements a pluggable mechanism. Each plugin is largely a category that implements the interface IModule. All plugins are loaded using reflection:
PcapAnalyzer (BLL)
The Business Logic Layer, responsible for analyzing network information (packet, TCP Session etc.), implements a pluggable mechanism. Each plugin is basically a class that implements the interface IModule. All plugins are loaded using reflection:
PcapProcessor (DAL)
As the Data Access Layer, this project is answerable forreading raw PCAP files using appropriate drivers (WinPcap, libpcap) and their wrapper library SharpPcap. Can analyze an inventory of files directly, and provides additional featuresjust like the reconstruction of all TCP Sessions (using the awesome project TcpRecon).
private void _initilyzeModulesList()
{
// Create an instance for any available modules by looking for every class that
// implements IModule.
this._modules = AppDomain.CurrentDomain.GetAssemblies()
.SelectMany(s => s.GetTypes())
.Where(p => typeof(IModule).IsAssignableFrom(p) && !p.IsInterface)
.Select(t => (IModule)Activator.CreateInstance(t))
.ToList();
// Register to each module event.
foreach(var m in _modules)
{
m.ParsedItemDetected += (s, e) => this.ParsedItemDetected(s, e);
}
}BruteSharkDesktop (PL)
Desktop application for Windows based on WinForms. Uses a cross-cutting project by the meaning it referrers both the DAL and BLL layers. This is done by composing each of the layers, register to their events, when the event is triggered, cast the event object to the next layer equivalent object, and send it to the next layer.
public MainForm()
{
InitializeComponent();
_files = new HashSet<string>();
// Create the DAL and BLL objects.
_processor = new PcapProcessor.Processor();
_analyzer = new PcapAnalyzer.Analyzer();
_processor.BuildTcpSessions = true;
// Create the user controls.
_networkMapUserControl = new NetworkMapUserControl();
_networkMapUserControl.Dock = DockStyle.Fill;
_sessionsExplorerUserControl = new SessionsExplorerUserControl();
_sessionsExplorerUserControl.Dock = DockStyle.Fill;
_hashesUserControl = new HashesUserControl();
_hashesUserControl.Dock = DockStyle.Fill;
_passwordsUserControl = new GenericTableUserControl();
_passwordsUserControl.Dock = DockStyle.Fill;
// Contract the events.
_processor.TcpPacketArived += (s, e) => _analyzer.Analyze(Casting.CastProcessorTcpPacketToAnalyzerTcpPacket(e.Packet));
_processor.TcpSessionArived += (s, e) => _analyzer.Analyze(Casting.CastProcessorTcpSessionToAnalyzerTcpSession(e.TcpSession));
_processor.FileProcessingStarted += (s, e) => SwitchToMainThreadContext(() => OnFileProcessStart(s, e));
_processor.FileProcessingEnded += (s, e) => SwitchToMainThreadContext(() => OnFileProcessEnd(s, e));
_processor.ProcessingPrecentsChanged += (s, e) => SwitchToMainThreadContext(() => OnProcessingPrecentsChanged(s, e));
_analyzer.ParsedItemDetected += (s, e) => SwitchToMainThreadContext(() => OnParsedItemDetected(s, e));
_processor.TcpSessionArived += (s, e) => SwitchToMainThreadContext(() => OnSessionArived(Casting.CastProcessorTcpSessionToBruteSharkDesktopTcpSession(e.TcpSession)));
_processor.ProcessingFinished += (s, e) => SwitchToMainThreadContext(() => OnProcessingFinished(s, e));
InitilizeFilesIconsList();
this.modulesTreeView.ExpandAll();
}BruteSharkCLI (PL)
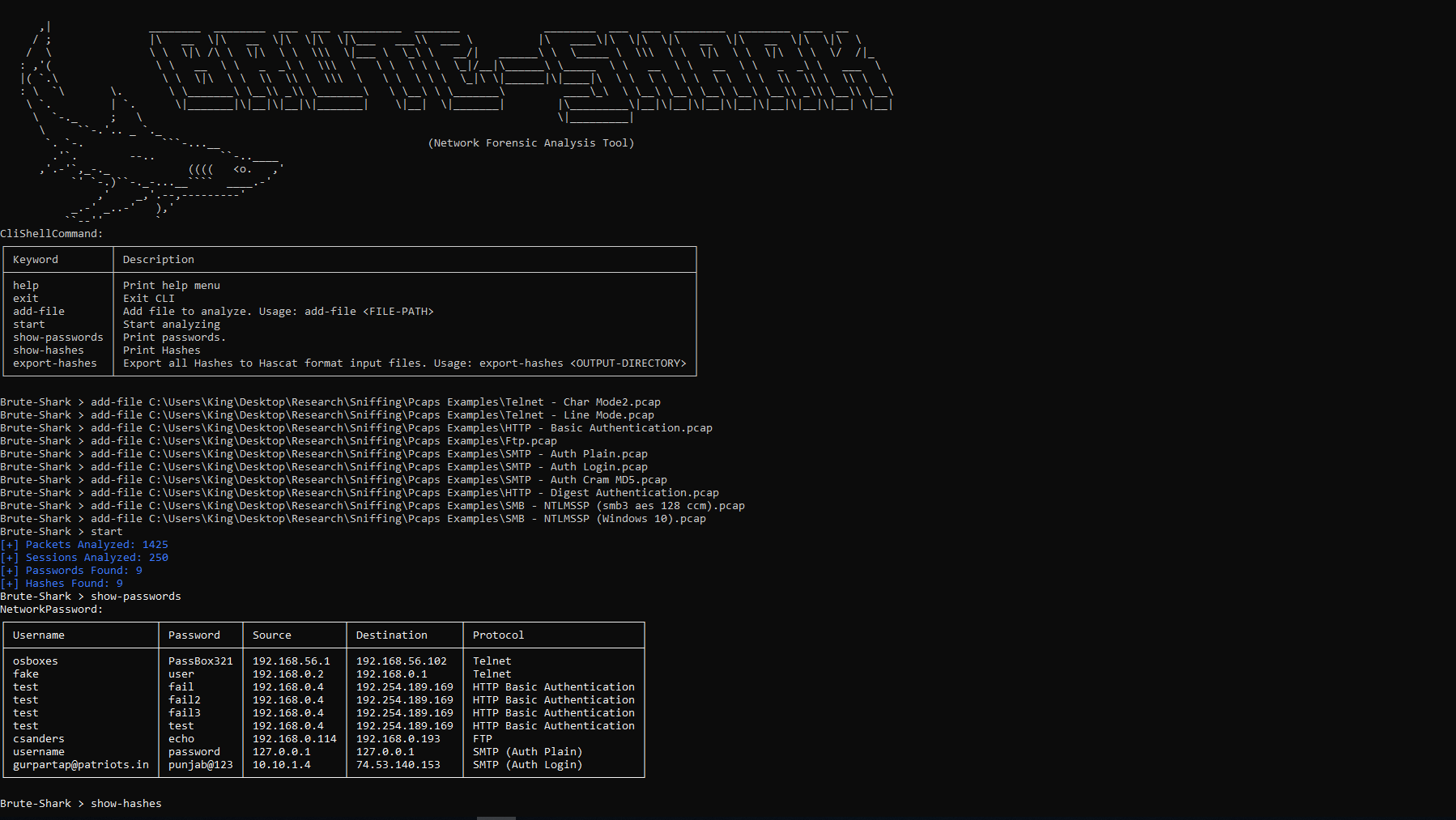
Command Line Interface version of Brute Shark. Cross platform Windows and Linux (with Mono). Available commands: (1). help
(2). add-file
(3). start
(4). show-passwords
(5). show-hashes
(6). export-hashes
(7). exit
More: https://github.com/odedshimon/BruteShark

No comments